Hey! Organisations don’t underestimate DMARC policy!
Hi friends,
It has been a long time since I have written, of course I am lazy. I was desperate to find bugs in Google & Facebook ( at least one valid ) so I thought let’s start with Google services. We all know about Google Groups, it is a service that provides discussion groups for people sharing common interests. Google Groups have a nice feature to post on groups by sending emails. At that time, I was logged in Google group by college email. Instantly, an idea popped up in my mind, “how does Google Group handles the emails from the domain that don’t have DMARC record setup ”.
DMARC ( Domain Message Authentication Reporting & Conformance ). It is a txt records on a DNS server. It’s task is to decide whether to accept or reject emails that fails SPF/DKIM. The unverified messages are handled according to DMARC policy.
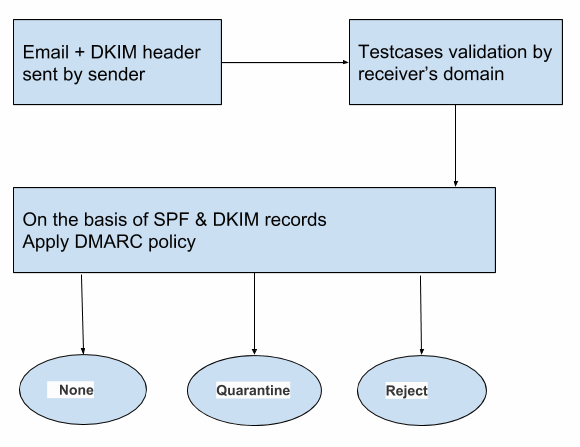
The sending domain should have an SPF and DKIM record before publishing DMARC record. SPF & DKIM are also txt records on a DNS server. SPF entry have list of servers that should be considered to send an email for specific domain while DKIM record is used for verifying message’s content. This is implemented by public and private key signing process. Cathy Patalas have written a nice blog about SPF & DKIM, if you want to get into details check it out https://blog.woodpecker.co/cold-email/spf-dkim/.
I was looking for the domain that don’t have DMARC record published. I chose my college domain and looked for the records using mxtoolbox https://mxtoolbox.com/dmarc.aspx. Fortunately/Unfortunately, there were no DMARC record found in my university’s DNS. I quickly used the service of smtp2go and sent an email to myself using my friend’s email address and I got message in my inbox.
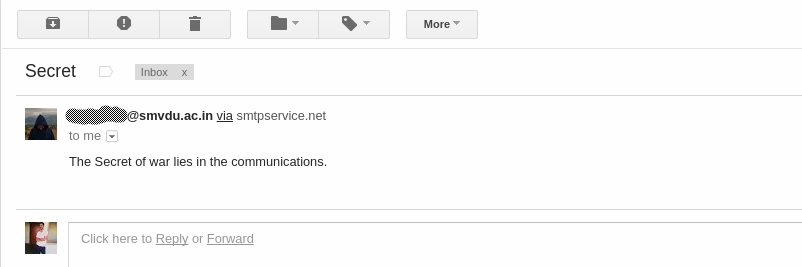
Finally, I had domain that don’t have DMARC record. For testing group functionality, I sent an email to my class Google Group using the service smtp2go. I found that Google Group allows the email from the domains that don’t have DMARC record that means an attacker can post as member using smtp service, if the email is known to the attacker.
Since this is an authentication bypass vulnerability, so I reported this to Google via their bug bounty program but they said it is an intended functionality. Now the question arises, Who is responsible for the security Organisations or Google ? I suggested a solution to Google security team.
If the email arrive from the domain that don’t have DMARC policy published then send an approval email to the sender’s email. Once authorized sender approve the post only then it should be posted on the group.
Reply from the security team
That solution would be too much hassle for most groups without any real security benefit.
I also contacted to our college V.C. sir and told him about the vulnerability. He pointed me to the respective authority in order to fix this vulnerability. So with the help of some faculty members & friends Ronij, Rajat I managed to add the DMARC policy to DNS server. For confirming the fix, I sent an email using the same service smtp2go. As you can see in the below image, email delivery got failed.
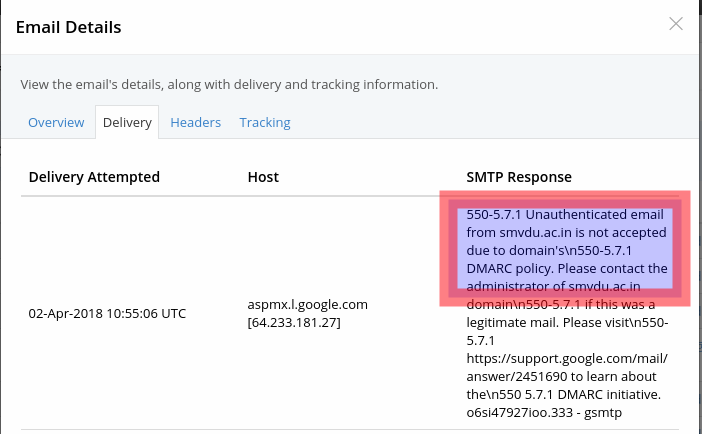
POC
Takeaway
While implementing features, always go through possible security checks for various functionalities in combination with other services to ensure that the functionality is working as intended. Everybody should be responsible for security.
Thanks you for your patience!